Single sign-on (SSO) with Microsoft clients allows cross-platform authentication between Web applications running in a WebLogic Server domain and browser clients (for example, Internet Explorer) in a Microsoft domain. The Microsoft clients must use Windows authentication based on the Simple and Protected Negotiate (SPNEGO) mechanism.
Cross-platform authentication is achieved by emulating the negotiate behavior of native Windows-to-Windows authentication services that use the Kerberos protocol. In order for cross-platform authentication to work, non-Windows servers (in this case, WebLogic Server) need to parse SPNEGO tokens in order to extract Kerberos tokens which are then used for authentication.
Weblogic Configuration
Setup
Active Directory Authentication Provider
It is recommended that the work to be carried out below should be secured as part of a script or build process.
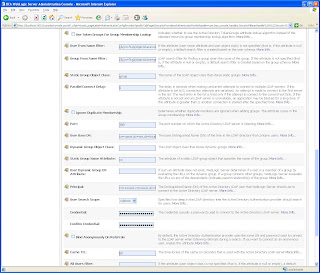
Navigate to Providers under Security Realms>myrealm and click New. Now create a new Active Directory Authenticator. Select the newly created authenticator and check that control flag has been set to SUFFICIENT.
Enter the Provider Specific tab and enter the following details:
| Attribute | Value |
| Group base DN | Location of groups in AD e.g. cn=groups,dc=myhost,dc=com |
| User Name Attribute | cn |
| User Object Class | user |
| Host | IP Address or host name e.g. 10.220.43.71 |
| Static Group DNs from Member DN filter | (&(member=%M)(objectclass=group)) |
| Static Member DN Attribute | DN |
| Attribute | Value |
| User from Name Filter | (&(cn=%u)(objectclass=user)) |
| Group from Name filter | (&(cn=%g)(objectclass=group)) |
| Static Group Object Class | group |
| Port | Port number AD is running on (usually 389 or 636 if in SSL mode) |
| User Base DN | Location of users in AD e.g. cn=users,dc=myhost,dc=com |
| Static Group Name Attribute | cn |
| Principal | A username within in AD which weblogic can use to authenticate – (e.g. cn=weblogic,cn=users,dc=myhost,dc=com) |
| credential | The password for the above user |
Confirmation
The users and groups from active directory should now exist in Weblogic, navigate to Users and Groups under Security Realms>myrealm to confirm:


AD & Client PC Configuration
The following software and hardware components are needed in order to create a single sign on environment:
| Hardware | Software |
| Active Directory Server | Microsoft Active Directory server software |
| Server running Weblogic Server with network connectivity to the Active Directory server domain | Weblogic Server 9.2 |
| Client PC – belonging to Active Directory server domain | Internet Explorer (or equivalent browser) |
Active Directory Setup
Create a Service Principal Name (SPN)
For each service or server that should be Kerberos enabled, a special user account must be created. This user account is called a Service Principal or SPN. This user acts as the connection between the Kerberos server, the Active Directory and the Identity Asserter in Weblogic.
The following example shows how a SPN user account is created in Active Directory.
Firstly start “Active Directory User and Computers” from the Administration tools menu.
Create a new user in the correct location in Active Directory – in the example below a user is being created in cn=users,dc=myhost,dc=com:

Enter the user details:
Hit next and enter the password for the user:

Uncheck the box that says the user must change their password at next logon and check the password never expires option.
Hit next and on the next screen hit finish.
Right click on the user name and go to the properties option. When the properties options appear select the account tab.
The ‘User logon name’ should:
- begin with “HTTP/”
- contain the hostname for the URL of the application e.g. www.myhost.com

Scroll down the account options list and check the box ‘Use DES encryption types for this account’. Click apply and then ok.
The password must now be changed as the DES encryption option has been chosen.
Right click on the username and select reset password:

Change the password and press OK.
The service principal is now created.
Create a KEYTAB file
A KEYTAB file contains “trust” information, which enables a trust relation between an external user or system and the Key Distribution Centre (KDC). This file contains a cryptographic key, which is used to encrypt the information between the server and the KDC.
The KDC will trust everything that is encrypted using this key. This means that the key must be stored securely on the application server. Only the application server should have access to this file.
The KEYTAB file is created using a utility from the Windows Resource Kit called “ktpass”. The ktpass program can create SPN bindings to a user account and export the trust information into a KEYTAB file. The ktpass utility will need to be installed (on the AD machine) and comes with the server software on CD (in /standard/support/tools/support.cab) or can be downloaded. Once installed the KEYTAB can be created by entering the following from a command prompt.
C:\ ktpass –princ HTTP/www.myhost.com@MYHOST.COM –mapuser “ssouser” –pass “password” –out ssouser.keytab –crypto des-cbc-md5
Where:
–princ is the User Logon name created in the above steps
-mapuser is the name of the user created above
-out is the name of the file created
Note: the domain (ie MYHOST.COM) must be in upper case. Take special care to enter the above line in correctly as incorrect details or a misspelled username can cause great trouble and frustration later.
A KEYTAB file named ssouser.keytab should now have been created and it will be used later in the Weblogic set up stage.
The setup can be tested by using the command setspn:
C:\>setspn -L ssouser
The output should look like this:
Registered ServicePrincipalNames for CN=ssouser,CN=Users,DC=myhost,DC=com:
HTTP/www.myhost.com
This shows that all Kerberos service tickets issued to the HTTP/www.myhost.com will be resolved to the SPN account.
Note that there should only be one registered SPN.
Client PC Setup
The Client PC must have Internet Explorer (or equivalent) browser. The instructions that follow are for Internet Explorer and should be applied for all agency users who will access the PC. In the production environment the settings should be created by scripts or via the build process.
Logon to the client PC (as a registered user in the Active Directory domain), open an Internet Explorer browser and go to tools>internet options

Select the local intranet icon and select sites.

When this box appears select advanced.

Add the spnego host to the trusted URLs.

Select the ‘Custom Level’ button.
Scroll to the bottom of the security settings and select the ‘Automatic logon only in Intranet zone’ option

If you have proxer server details to configure follow these steps:
Go to tools>internet options>connections>LAN settings

Then click the advanced tab and add the spnego host URL to the exceptions list

Proxy server configuration is now complete.
Select the advanced tab and confirm that ‘Integrated Windows Authentication’ has been enabled:
In order that the browser can see the SPNEGO host the host name www.myhost.com needs to be added to the DNS server or the hosts file on the pc.
WebLogic Server Setup
JDK Configuration
The following files need to be added to the domain directory of the Weblogic Server.
krbLogin.conf - JAAS login config
ssouser.keytab – SPN KEYTAB (created earlier)
The krbLogin.conf looks like this:
/**
* Login Configuration for JAAS.
*/
com.sun.security.jgss.initiate {
com.sun.security.auth.module.Krb5LoginModule required
principal="HTTP/www.myhost.com@MYHOST.COM" debug=true useKeyTab=true
keyTab=ssouser.keytab storeKey=true useTicketCache=true;
};
com.sun.security.jgss.accept {
com.sun.security.auth.module.Krb5LoginModule required
principal="HTTP/www.myhost.com@MYHOST.COM" debug=true useKeyTab=true
keyTab=ssouser.keytab storeKey=true useTicketCache=true;
};
Where:
- Principal is the User Logon name created in 3.1.1.
- keyTab is the name of the keytab file created in 3.1.2.
The URL for the application in this example is:
http://www.myhost.com:7001/webapp/restricted/test.jsp
In the web.xml file of the application the following lines have been added to restrict content, those in bold are specific to the SSO setup:
Restricted Area
WebLogic Server start script
The following adjustments need to be made to the startWeblogic.cmd (or .sh) script:
Create the following environment entries:
Set KERB_OPTIONS= -Djava.security.krb5.realm=MYHOST.COM -Djava.security.krb5.kdc=activedirectory.MYHOST.com -Djava.security.auth.login.config=krbLogin.conf -Djavax.security.auth.useSubjectCredsOnly=false -Dweblogic.security.enableNegotiate=true
Where:
- activedirectory.MYHOST.com represents the location of the Active Directory Server
- krbLogin.conf is the name of the file created in 3.3.1.
Configuring WebLogic Security Asserters
The work to be carried out below should be secured as part of a script or build process.
Launch the Weblogic console:
Navigate to Providers under Security Realms>myrealm:
Click on New and select a “NegotiateIdentityAsserter”:
Select the newly created Identity Asserter, the details should be as below:
Enter the Provider Specific tab and ensure that Form based authentication has not been selected:
Authentication Control
Select the Default Authenticator and change the control flag so that it says
‘SUFFICIENT’
Press apply
Select the default identity asserter,
At the bottom of the screen in the available column select Authenticated user and press the right arrow followed by apply.
Ordering Authentication Providers
Reorder the authentication providers such that they are in this order:
Debugging
It is possible to debug SSO in Weblogic 9.2. The debug can be found in the